IBM Sterling Secure Proxy
While file transfer over the Internet is cheap, it can also be highly insecure. IBM Sterling Secure Proxy (SSP) enables you to leverage the cost benefits of using the Internet for file transfer while ensuring the security of your file transfer infrastructure by ensuring your firewall is secure. SSP protects your internal network from malicious attacks that may negatively impact your business and interrupt business processes.
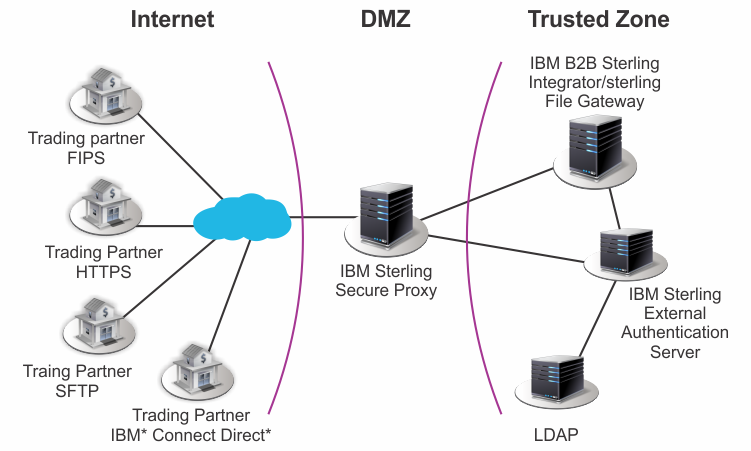
SSP is a demilitarized zone (DMZ)-based application proxy that protects your file transfers from the public Internet, by enforcing tight controls including trading-partner authorization, multi-factor authentication and session break, before the transfer ever enters your trusted zone
- SSL session breaks and multi-factor authentication – Help guard against unauthorized access and reduce data vulnerability to protect your brand
- Leverage the Internet – Lower your file transfer costs and grow your file transfer community while securing the data and access to your trusted zone
- Firewall navigation best practices – Increases perimeter security for your file transfer infrastructure to comply with regulatory policies and pass tougher security audits
- Self-service logon portal – Provides self-service password management for trading partners reducing the dependency on IT staff
- Sterling Secure Proxy is available as licensed on premise software.
Application Proxy:
Resides in the demilitarized zone (DMZ)Supports IBM® Sterling Connect:Direct®, IBM® Sterling Connect Express® and IBM® Sterling B2B Integrator servers
Support for multiple DMZ environments
Supports FTP, FTPS, HTTP, HTTPS, SSH/SFTP, PeSIT and Sterling Connect:Direct protocols
Supports use of a FIPS 140-2 compliant data encryption module
Firewall Navigation Best Practices:
Prevents inbound holes in the firewallMinimizes rich targets in the DMZ by ensuring that files, user credentials and data are not stored in the DMZ
Establishes sessions from more-trusted to less-trusted zones
Enforces internal and external security policies
Perimeter Security:
Prevents direct communications between external and internal sessions by establishing secure session breaks in the DMZ using SSL or TLSInspects protocol and sensitive control information, enabling configurable error handling for violations
Session limits and data encryption guard against Denial-of-Service attacks
Authentication Services:
Customizable logon portal provides self-service password management for trading partnersSupports single sign-on and integrates with existing security infrastructure, including Active Directory and Tivoli user databases
Multifactor authentication enforces tight controls and validation of trading
partner identity in the DMZ before information is passed to the trusted zone
Authentication options include IP address, user ID and password, digital certificates, SSH Keys, RSA SecurID
Clustering:
One central configuration manager pushes out configuration rules to multiple engines running in the DMZ, making it easy to scaleClustering for high availability and load balancing provides operational continuity and improved performance